- Read the documentation on how to create links or track sale conversions.
- Learn how to integrate Dub into your application.
- Reach out to us to feature your integration in the integrations marketplace.
Integrating via OAuth 2.0 (recommended)
Dub supports OAuth 2.0 authentication, which is recommended if you build integrations extending Dub’s functionality. We recommend you use a OAuth client library to integrate the OAuth flow. You can find recommended libraries in a variety of programming languages here.OAuth endpoints (
/oauth/authorize, /oauth/token, /oauth/userinfo) are
not available in the Dub SDKs. You’ll need to call these endpoints directly
using HTTP requests or an OAuth client library.Set up OAuth 2.0
Here is a step-by-step guide on how to set up OAuth 2.0 authentication with Dub.Create an OAuth2 application in Dub
- Go to the OAuth Apps tab in your workspace.
- Click on Create OAuth App.
- Fill in the required fields to create an OAuth2 application.
Redirect users to authorization URL
When you want to authenticate a user, you need to redirect them to the Dub OAuth authorization URL.Parameters:
An example URL would look like this: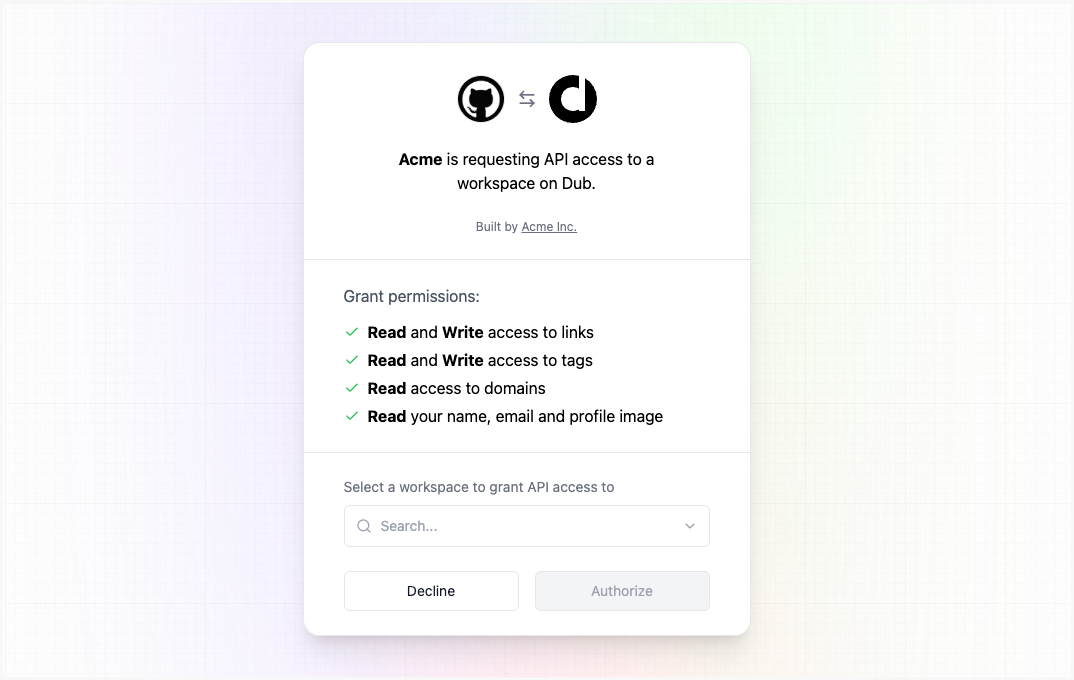
| Property | Description |
|---|---|
client_id | The client ID of your OAuth application. |
redirect_uri | The URL to redirect the user to after they authorize the application. Make sure this URL is registered in your OAuth application. |
response_type | Expected response type. It should be code. |
scope | A space separated list of scopes that you want to request access to. Read more about scopes here. |
state | The state parameter to prevent against CSRF attacks. Read more about it here |
code_challenge | Required for PKCE. The code challenge generated from the code_verifier. |
code_challenge_method | Required for PKCE. The method used to generate the code challenge. It should be S256. |
PKCE (Proof Key for Code Exchange) is enabled by default and recommended for all applications. If you include
code_challenge and code_challenge_method in the authorization request, you must also include the code_verifier when exchanging the code for an access token in Step 3.
Exchange code for an access token
The Response:After a successful request, you will receive a JSON response with the access token.
code parameter is returned in the query string when the user is redirected back to your application. You can exchange this code for an access token by making a POST request to the Dub OAuth token URL.- With PKCE (recommended)
- With client secret
We recommend using the PKCE flow for all applications, especially native desktop or mobile applications and single-page apps (SPAs) where the Parameters:
For example, the Dub Raycast extension uses PKCE to authenticate users.
client_secret cannot be hidden.With PKCE, the client_secret is never sent to the authorization server, preventing the client_secret from being leaked from the client application.| Property | Description |
|---|---|
code | The code you received when the user was redirected back to your application. |
client_id | The client ID of your OAuth application. |
code_verifier | The original code verifier used to generate the code_challenge in Step 2. |
redirect_uri | The same redirect URI you used in the authorization URL. |
grant_type | The grant type. It should be authorization_code. |
Retrieve user and workspace info
After obtaining an access token, you can retrieve information about the authenticated user and their workspace by calling the userinfo endpoint:Here’s an example using curl:Response:
Make an API request with the access token
Once you have obtained a valid access token, you can use it to make requests to the Dub API.You can initialize Dub SDK with the access token.Here is an example of how you can create a link using the Dub TypeScript SDK:Or pass the access token in the header:
Authorization: Bearer <ACCESS_TOKEN>Refresh the access token
Dub access tokens are short-lived, depending on the Parameters:
Response:After a successful request, you will receive a JSON response with the new access token.This will invalidate the old access token and refresh token.
expires_in value (the default value is 7,200 seconds, or 2 hours). Dub will respond with 401 Unauthorized if you try to use an expired access token.To refresh the access token, you need to make a POST request to the Dub OAuth token URL with the refresh_token you obtained when exchanging the code for an access_token.| Property | Description |
|---|---|
client_id | The client ID of your OAuth application. |
client_secret | The client secret of your OAuth application. |
grant_type | The grant type. It should be refresh_token. |
refresh_token | The refresh token you received when exchanging the code for an access token. |
Scopes
You can request access to specific scopes when redirecting users to the Dub OAuth authorization URL. Scopes are permissions that the user needs to grant to your application. Dub supports the following scopes for OAuth 2.0:| Scope | Description |
|---|---|
links.read | Read access to links. |
links.write | Write access to links. |
tags.read | Read access to tags. |
tags.write | Write access to tags. |
analytics.read | Read access to analytics. |
domains.read | Read access to domains. |
domains.write | Write access to domains. |
folders.read | Read access to folders. |
folders.write | Write access to folders. |
user.read | Read access to user information. This scope is included by default. |